Red Sea Shoot-Downs Offer Hugely Valuable Lessons, Also Pose Big Intel Risk

Dozens of recent shoot-downs over and around the Red Sea have provided an unprecedented amount of data on the performance of the U.S. Navy's sprawling air warfare apparatus. It's not just the United States that can leverage these events for critical insights. Adversaries, specifically China, can, as well.
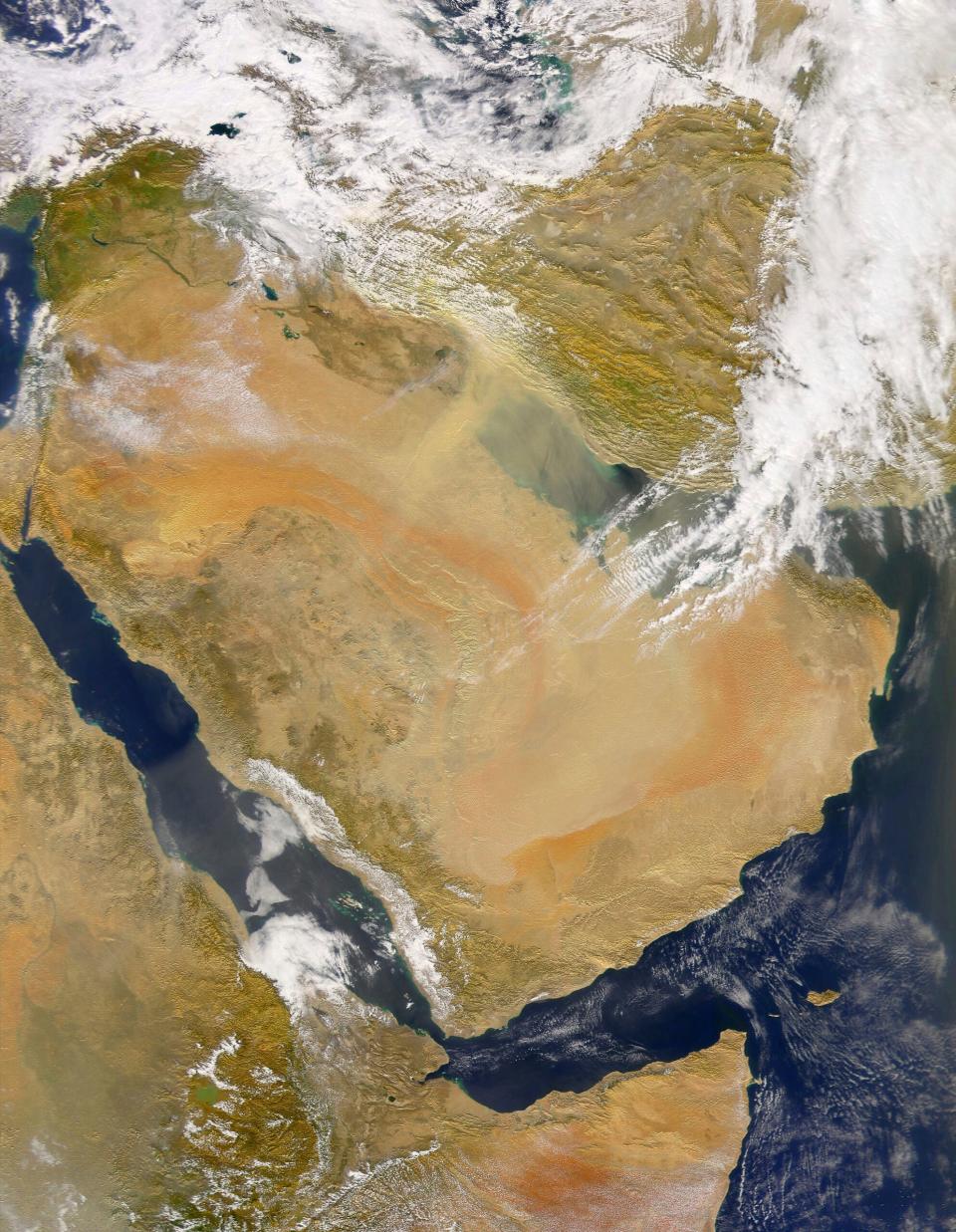
The swatting-down of many Houthi cruise and ballistic missiles, as well as dozens of drones, by U.S. Navy destroyers, as well as F/A-18E/F Super Hornets, has resulted in a real-world stress test of the Navy's air warfare enterprise. Never before has there been so much real-world data to leverage of engagements across a wide array of target types and scenarios. This is also happening in a complex littoral battlespace, making that data even more valuable.
All this information, including every aspect of each individual engagement, will be pored over and used to improve the ever evolving Aegis Combat System that underpins the Navy's air-warfare capabilities, as well as all the sensors, weapons, and platforms that 'plug into it' via advanced networking.
The Navy fields the most complex air warfare capability on the planet. At its heart is the aforementioned Aegis combat system that is integrated into the service's destroyers and cruisers. A stripped-down version of this system (COMBATSS-21) is also found on Littoral Combat Ships and is set to be used on Constellation class frigates.

The Aegis combat system leverages a wide array of shipboard sensors, with the SPY-1 phased array radar system being its primary sensor, and it controls most of the arsenal of weapons housed on the ships it is installed on. It also 'talks' to pretty much everything else in the fleet, such as MH-60 Sea Hawk helicopters. This also includes carriers and their air wings' fighters and all-important E-2 Hawkeye airborne warning and control aircraft. Many sources of off-board data not exclusive to the Navy can also be piped into the system via datalink. An elaborate web of waveforms that make up a complex networking architecture connects it all together in an increasingly seamless fashion in order to dominate the battlespace.
Read all about the Aegis combat system and where it is headed in our feature linked here.
Suffice it to say that putting all this to use in repeated real-world engagements that incorporate sea, air, and space-based assets, and includes the firing of actual weapons, all in a confined geographical area, is a very unique opportunity.
The crisis off Yemen's shores also marks a number of firsts that has a huge impact on the quality and importance of data being gathered. It marks the inaugural firing of anti-ship ballistic missiles (ASBMs) in anger. While a wide array of ASBM systems are now proliferating with different militaries around the globe — most of which are potentially hostile to the U.S. and its allies (primarily China) — they have never actually been used in combat. Firing these weapons repeatedly, and engaging some of them with the weapons on Navy destroyers, is giving a real world look at how these engagements actually occur.
Check out our complete rundown on the anti-ship missiles the Houthis are firing at warships and commercial shipping in and around the Red Sea in our recent feature linked here.

The same can be said for large volumes of drones, which is a newer and rapidly developing threat class that can blur the definition between unmanned systems and missiles. Also, drones have disparate performance and signature characteristics compared to traditional missiles, including flying at low speeds and at lower altitudes, while also possessing very small radar cross-sections and infrared signatures. These characteristics can fall below the filters on radar systems traditionally put in place to filter out clutter, for instance. The sheer volume of drones and the consumption of effectors used to intercept them has been especially unique to this crisis. Layering these threats together with anti-ship cruise and ballistic missiles and small boat attacks makes countering them even tougher.
This operation also saw a relatively confined area with complex littorals being defended via multiple surface combatants, including a handful of NATO allies' ships. It also saw the incorporation of the aforementioned USS Dwight D. Eisenhower's air wing in the counter-air operation. The E-2 Hawkeye provides critical 'look down' capability, especially for spotting low-flying and small radar signature targets, as well as networking and command and control functions. Super Hornets were also successfully leveraged on multiple occasions to engage some of the threats fired by Houthi militants. Navy MH-60S/R Sea Hawk helicopters were called upon to engage small boats with their air-to-surface strike and force protection armament. So, this was a remarkably complex operation against a foe that had the ability to fire many weapons of multiple types in sustained layered attacks.
All this data can now be compared to simulations, war game results, training events, exercises, and live and virtual weapons testing. Improvements can then be made to the Navy's counter-air ecosystem of software, sensors, weapons and sailors. Moves can be made to plug capability gaps and to double-down systems that proved highly capable or even more valuable than previously thought. Refinements in software can be made to help crews better tackle future threats. Tactics and procedures can be evolved and best practices can be refined.
The loadouts of Navy surface combatants — what weapons take up precious real estate in their vertical launch system cells — will also be reviewed and refined based on this crisis. The sheer quantitative problem that drones present these ships with will likely be more heavily factored going forward. Just firing this many missiles also provides critical data on their effectiveness and can help identify efficacy and readiness issues with different rounds. Gauging how well various electronic warfare 'soft kill' systems on these ships performed against desperate threats and at what distances, where applicable, will also be hugely valuable as the Navy drastically expands its fleet's electronic warfare capabilities.

While updated hardware and software are absolutely crucial to modern Naval operations, people are still arguably its most critical factor. The U.S. Navy will be in a far better place to train its sailors and aviators to confront similar threats successfully it the future via lessons learned in recent weeks, which can be disseminated throughout the fleet and trained for in exercises.
Finally, what assets that other services provided to the mission proved to be highly valuable and which ones less so? This information will be critical to tailoring future packages of joint capabilities for naval-dominant operations.
On the other hand, America's adversaries are undoubtedly capitalizing on these events and watching them very closely in an area of the world that is already under constant surveillance. Having the U.S. Navy engaging many targets for hours on end using much of what it has in its quiver allows for adversaries to watch and especially listen across the electromagnetic spectrum. The complex web of waveforms and sensor signatures, operating in full combat modes, can all be hoovered up and analyzed. Movements of ships and recording the weapons they fire at certain types of targets, and the emissions that guide those weapons, are all extremely important intelligence that an adversary would want. This is not just for a potential foe to defend against those capabilities and to produce countermeasures to them, but especially to emulate and design its own weapons, sensors, and communications infrastructure based on them. This is especially crucial for the People's Liberation Army Navy (PLAN) that is rapidly expanding and seeking to reach qualitative parity with the U.S. Navy at great cost. Other adversaries and friends alike are also surely taking an interest in the potential intelligence windfall from these events.
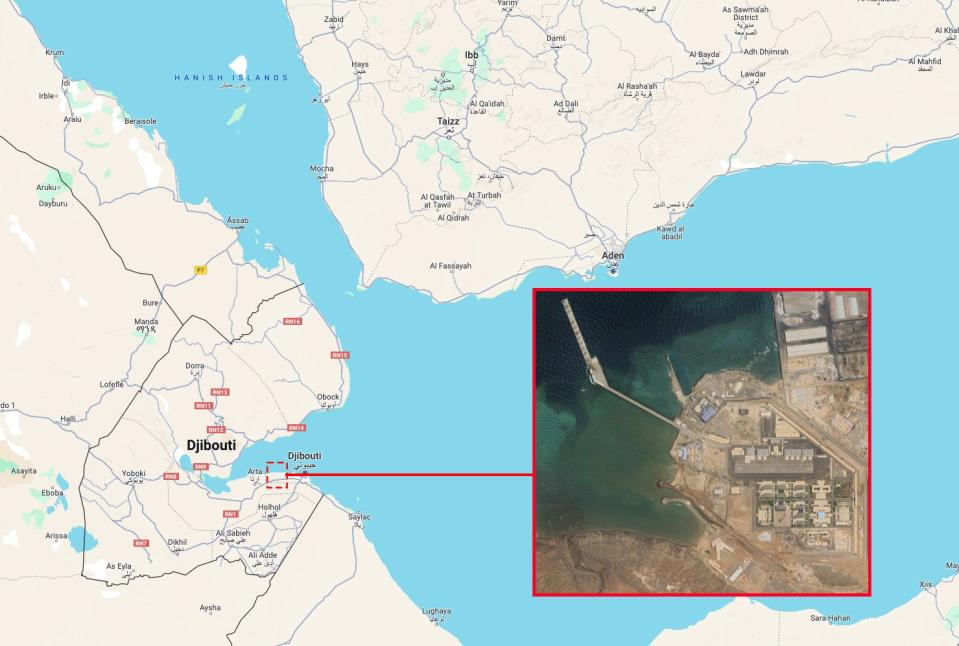
China has a major base right along the southern approach to the Bab el-Mandeb Strait, in Djibouti. This installation serves many functions, from major naval support facility to an intelligence collection hub. The base sits just 80 miles from Yemeni shores. In addition, China has naval ships in the region on a near constant basis, along with other vessels that are not necessarily as clearly delineated. Manned aircraft and drones can also be used to collect critical intelligence, as well as space-based systems.
Since the U.S. and the U.K. have struck back against the Houthis, now actual offensive combat operations can also be observed. The U.S. has now struck targets three times in Yemen, with the latest being launchers with missiles which were being prepared to launch. This would indicate that a preemptive, time-sensitive targeting operation is now underway to stop the attacks before they start. As we have repeatedly noted, doing this to any robust degree would be very resource intensive, and could require many more assets and capabilities than what were previously in play in the region. All of these reconnaissance and strike operations can be closely observed now, as well.
In other words, for China and other adversaries, they are getting the opportunity to see how the U.S. Navy and some of its allies actually fight. A significant portion of the entire spectrum of combat operations are being ran through their paces in real world circumstances. Live weapons are being fired en masse.
It's a windfall of intelligence.
The fact that this has gone on for many weeks now means that assets could have been moved into the region to enhance collection efforts. The area where this is all occurring is also uniquely ideal for surveillance, with relatively tight waterways, meaning it is easy to find and surveil targeted assets, even from the shore in some cases.
So there you have it. While the U.S. Navy and its allies are definitely executing an absolutely fundamental mission set — keeping the sea lanes open to trade — they are also providing unprecedented data on the effectiveness of their systems under challenging combat conditions. At the same time, they are also providing an equally unprecedented opportunity to potential foes to gain insights onto how the Navy operates in such a complex battlespace and all the critical electronic signatures and tactics that go along with it.
It's truly a double edged sword, but anything lost to foreign collection is likely eclipsed by the enhancements in technologies and tactics that will come out of the crisis.
Contact the author: [email protected]